The Art of Overkill: Web Dev Edition
“The chief enemy of creativity is ‘good’ sense.” — Pablo Picasso.
Hello, fantastic developers! I am thrilled to write about a topic that’s near and dear to my heart: over-engineering. Ah, the art of complicated, simple things — a craft many of us have perfected over the years. Today, I’m excited to share a guide that will take this art form to a new level.
Have you ever thought building a simple website showcasing your grandma’s cookie recipes was too easy? Have you ever felt the urge to throw in a few extra layers of complexity just for fun? Well, you’re in the right place. In this blog, we’ll explore how to build a simple website the RIGHT WAY — that is, by going so far above and beyond what’s necessary that it borders on the absurd. Think of it as using a sledgehammer to crack a nut or, perhaps, using a bazooka to kill a fly.
Why am I so happy to write about this? Because it’s high time we celebrate the overachievers among us. Those who look at a simple task and say, “How can I make this more complicated?” This blog is for you, and I can’t wait to dive into this labyrinth of unnecessary complexity together.
So, without further ado, let’s get started on this journey of over-engineering a simple website. Buckle up; it’s going to be an unnecessarily complicated ride!
Hosting Havoc: Where Buckets Overflow and Caches Never Expire
Ah, hosting — the cornerstone of any website. But why settle for simplicity when you can turn this foundational aspect into an intricate web of services? Let’s break it down.
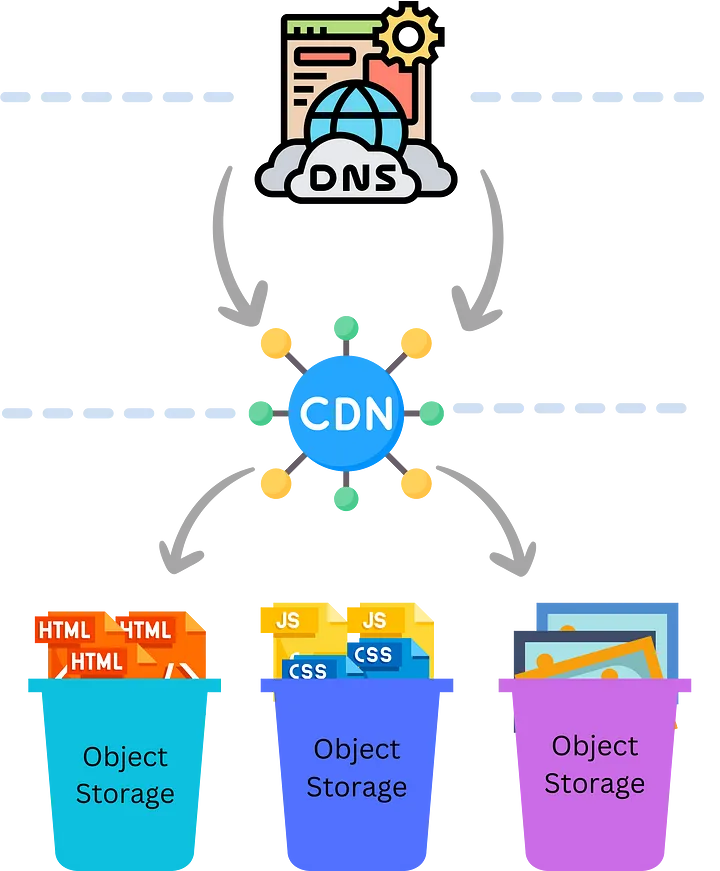
Object Storage: The Bucket Brigade
First things first, you’ll want to host your 10-page website in an Object Storage service. But let’s not be pedestrian about it. Separate your HTML, images, CSS, and JS into different buckets. Because, you know, segregating your data types is the first step toward enlightenment.
CDN: The Speed Illusionist
Next, front your object storage with a Content Delivery Network (CDN). You might think caching is for websites with high traffic, but why not give your grandma’s cookie recipes the VIP treatment? After all, those chocolate chip cookies deserve to be delivered at lightning speed, even if no one is actually requesting them.
DNS Management: The Name Game
Finally, let’s talk about DNS. Use a dedicated DNS service to manage your domain names. Why? More services mean more complexity, which means you’re doing it right — or so you’d like to think.
API Alchemy: Turning Simple Calls into Containerized Conundrums
Ah, APIs — the magical gateways that let your website communicate with the outside world. But why make straightforward API calls when you can wrap them in layers of unnecessary complexity? Let’s explore.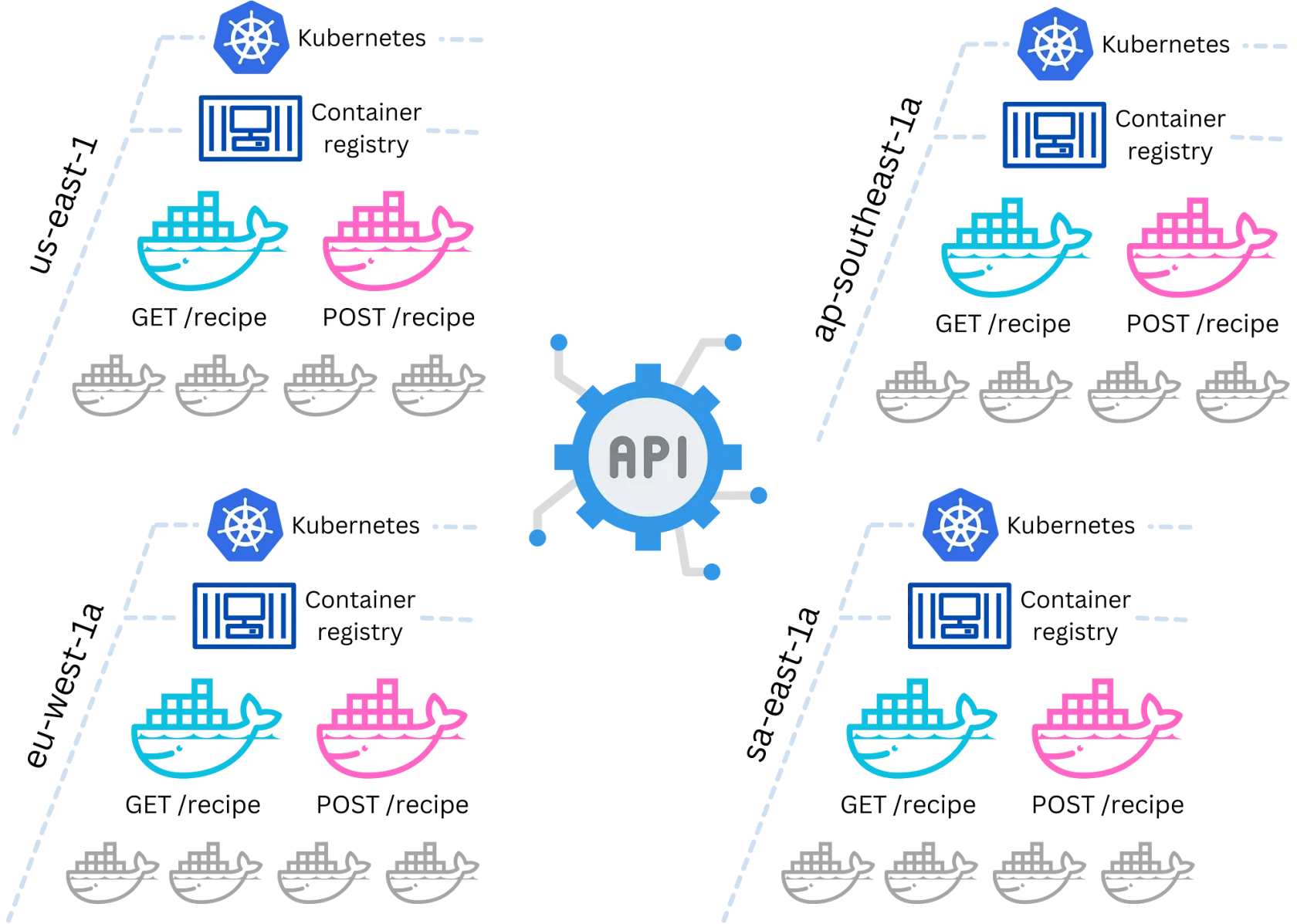
API Alchemy: Turning Simple Calls into Containerized Conundrums
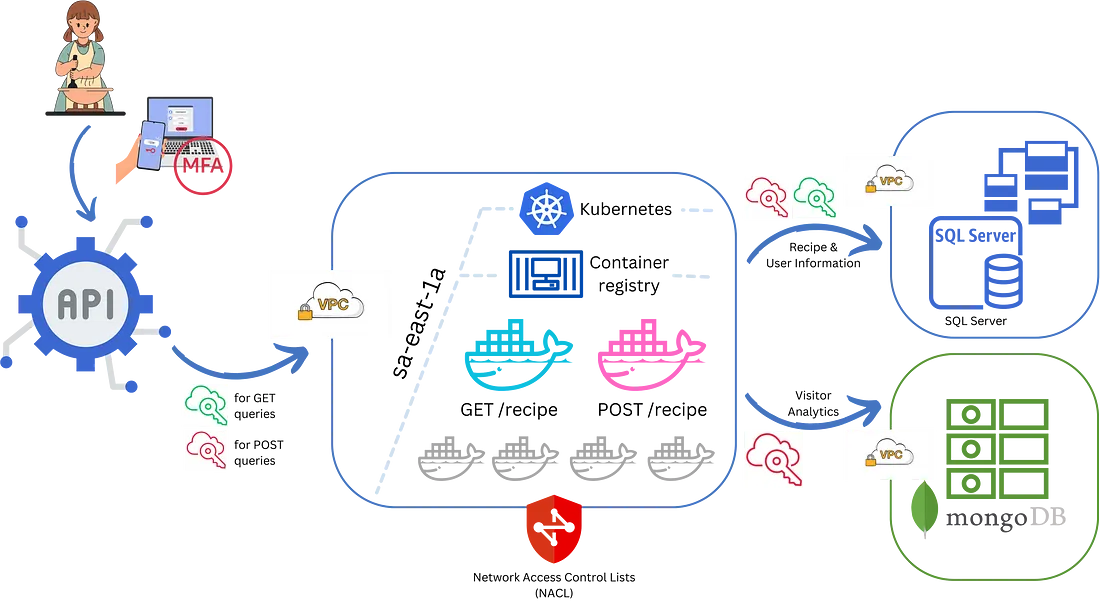
API Management: The Unnecessary Middleman
First on the list is API Management. You might think a simple website doesn’t need an API gateway, but that’s where you need to correct. Implement an API Management service as the unnecessary middleman between your website and your APIs. Add rate limiting, caching, and analytics features you’ll never need. Your developer friends will be scratching their heads, wondering why you went to such lengths. And that’s precisely the point.
Containers and Docker: The Russian Dolls of Software
Now, let’s talk containers — not just any containers, but Docker containers. Could your APIs be simple serverless functions? Absolutely. But why opt for simplicity when you can add another layer of complexity? Build Docker images for each of your APIs and push them to a Docker Registry. Nothing says “I’m a serious developer,” like using Docker containers for a project that doesn’t need them.
By using Docker, you’re not just containerizing your APIs but also making a statement. A statement that says, “I can make even the simplest of tasks complicated.” And let’s be honest, that’s an achievement in itself.
Kubernetes: Orchestrating the Overkill
Once your containers are ready, it’s time to manage them. And what better way to do that than with Kubernetes? Deploy your containers on a Kubernetes cluster and scale them across multiple availability zones. You’ll be paying for virtual machines you don’t need, but hey, it’s all in the name of over-engineering.
Streaming and Queues: Where Data Rivers Meet Traffic Jams
Ah, data streams and message queues — the tools that make your architecture robust and scalable. But let’s be honest, they can also ridiculously complex a simple project. And that’s precisely what we’re aiming for.
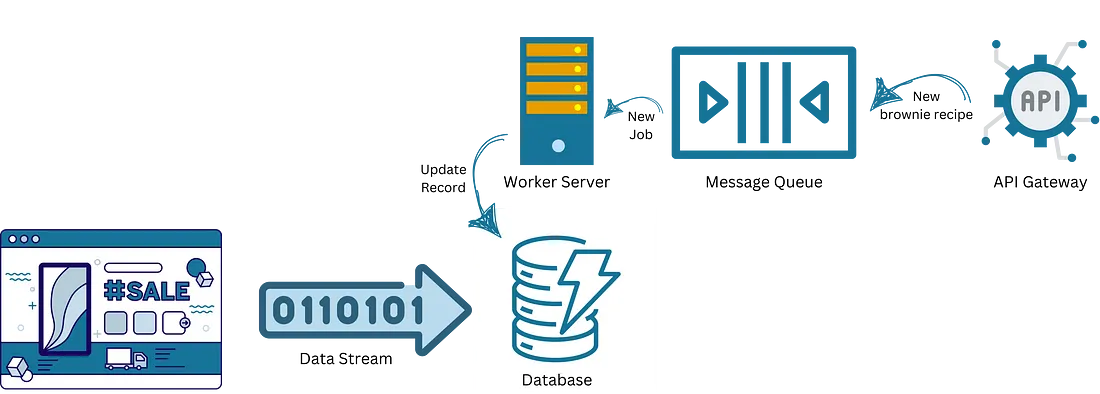
Data Streams: The Unread Diaries
First up, data streams. Streaming is for real-time analytics or large-scale data processing. But why not use it for your grandma’s cookie recipe website? Implement a Data Streaming service to ingest all your site analytics that no one will ever look at. Create separate streams for page views, button clicks, and mouse hovers. Clearly, you need to know the second someone contemplates clicking on your oatmeal raisin cookie recipe.
Message Queues: The Overkill Post Office
Next, let’s talk about message queues. Whenever grandma adds a new recipe, don’t just update the website — send it through a Message Queue. Use the queue to decouple your recipe publishing pipeline, adding unnecessary latency and an air of architectural sophistication. Process recipes asynchronously because real-time is too mainstream.
Imagine this: Grandma’s new brownie recipe goes into a queue and gets processed by a series of unnecessarily complex microservices before finally appearing on the website. It’s not just a brownie recipe; it’s a journey through your over-engineered architecture.
Databases: The Overstocked Libraries of Unread Books
Ah, databases — the backbone of any application and the treasure trove of over-engineering opportunities. Why settle for one type of database when you can have them all? Let’s explore this labyrinth of data storage options.
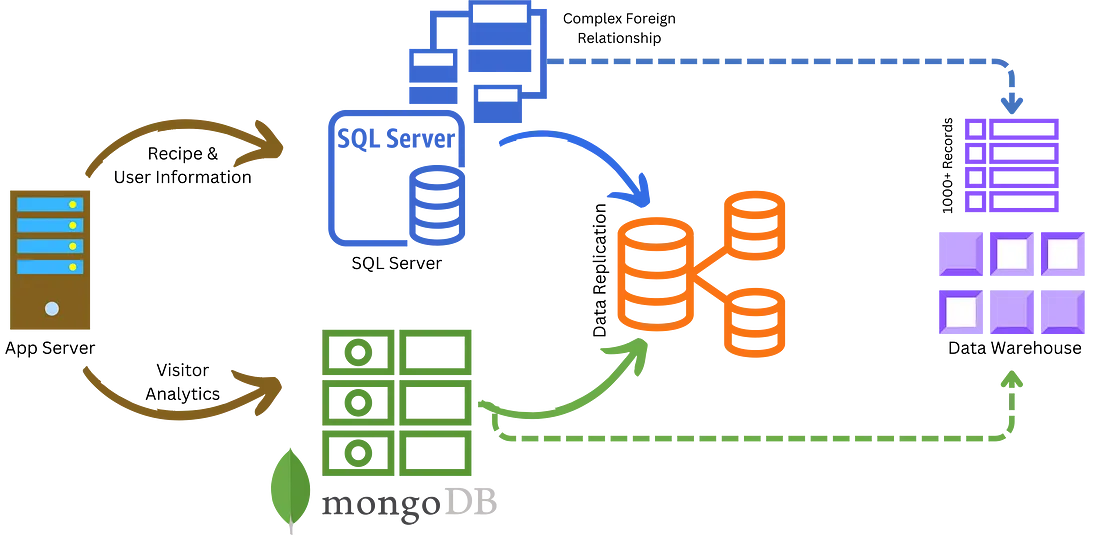
NoSQL: The Hoarder’s Paradise
First up is NoSQL. Perfect for storing unstructured data, but let’s take it up a notch. Use a NoSQL database like MongoDB or Cassandra to track every visitor interaction in real-time. Did someone hover over a chocolate chip cookie recipe for 3.2 seconds? Into the database, it goes. You can later use this goldmine of irrelevant data to hyper-personalize recipe recommendations or, more likely, never look at it again.
SQL: The Over-Organized File Cabinet
Next, let’s talk about SQL databases. Go ahead and set up a relational database like PostgreSQL or MySQL for your mailing list, user accounts, and any other structured data. But don’t just stop there; create multiple tables with complex relationships and foreign keys for data that will never be related. And, of course, replicate this database across multiple availability zones because you never know when a disaster might strike your grandma’s cookie recipes.
Data Warehouse: The Unused Gym Membership
Last but not least, introduce a Data Warehouse into the mix. Use a service like Snowflake or BigQuery to store the same data you’re already storing in your other databases. The point isn’t to use the data warehouse effectively; it’s to have and pay for it. Your 1,000-row Excel sheet will query blazing fast now, and that’s what really matters, right?
Search Engines: The Overkill Oracle of Obscure Queries
Ah, full-text search engines — the tool you never knew you needed for your grandma’s cookie recipe website. But why settle for a simple search bar when you can implement a full-blown search engine that rivals Google and Bing? Let’s dive in.
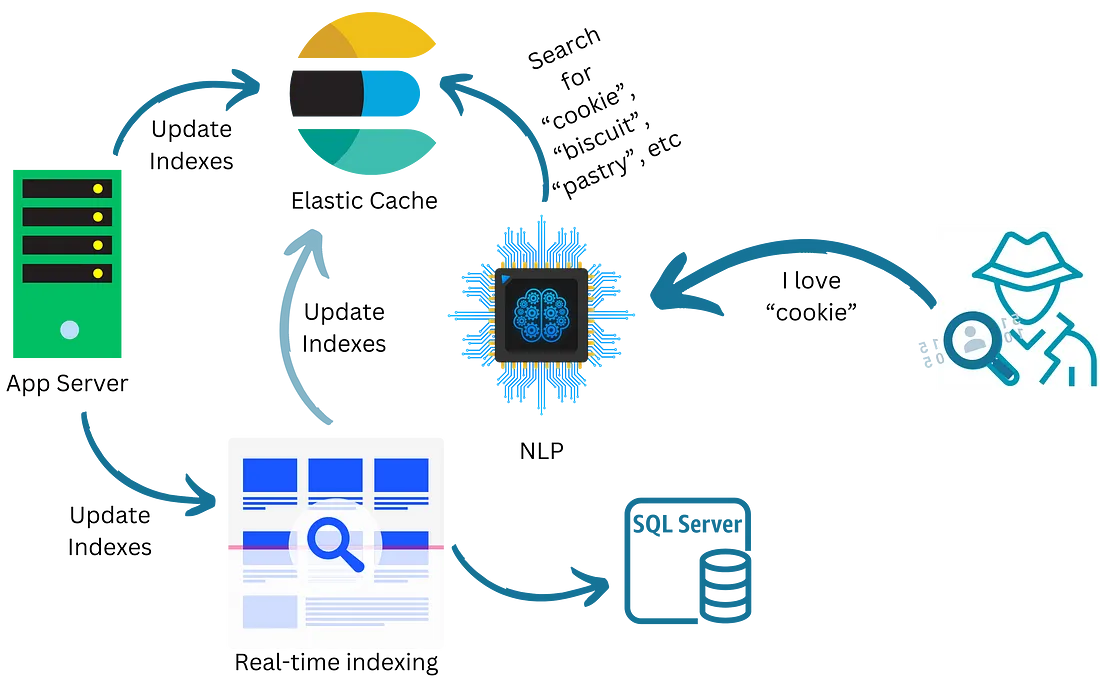
Elasticsearch: The Needle Finder in a Haystack
First on our list is Elasticsearch. This powerful search engine can handle complex queries, real-time indexing, and more. But for our purposes, we’ll use it to find recipes. Imagine typing “chocolate” and getting not just every recipe that includes chocolate but also every instance where the word “chocolate” appears in the comments, the user reviews, and even the metadata. It’s overkill at its finest.
NLP and Query Expansion: Because Simple is Boring
Why stop at essential keyword matching when you can introduce Natural Language Processing (NLP) into your search functionality? Use query expansion techniques to include synonyms, misspellings, and related terms. Now, a search for “cookie” could also bring up results for “biscuit,” “pastry,” and “snack.” It’s entirely unnecessary for a simple recipe website, but that’s the point.
Real-Time Indexing: The Overzealous Librarian
As if that’s not enough, let’s add real-time indexing to the mix. Every time Grandma adds a new recipe, or someone leaves a comment, it gets indexed in real time. Because when someone is desperately searching for a brownie recipe at 2 a.m., they need to see that new comment about adding extra walnuts, right?
Security: The Fort Knox of Cookie Recipes
Ah, security — the realm where paranoia meets complexity. Why have a simple, secure website when you can build a digital fortress that would make even the Pentagon jealous? Let’s explore the over-engineered world of network isolation and identity management.
Network Isolation: The Unreachable Island
First up, let’s talk about network isolation. Wrap your entire architecture in a Virtual Private Cloud (VPC) with multiple subnets across different availability zones. But continue there; create separate VPCs for your front-end, back-end, and databases. Implement Network Access Control Lists (NACLs) and security groups so stringent that even authorized users will have difficulty getting in. It’s like building a moat, a wall, and a drawbridge for a treehouse.
Identity Management: The Maze of Permissions
Next, let’s delve into identity management. Create individual roles for every conceivable action on your website. Want to view a cookie recipe? You’ll need the ViewRecipe role. Do you want to leave a comment? That requires the CommentAuthor role. And let’s remember Multi-Factor Authentication (MFA). Require MFA for any action more significant than scrolling down the page.
Imagine this: To access a recipe with chocolate, you’ll need to go through a two-step verification process that involves receiving a code on your phone and answering a security question about your favorite type of chocolate. It’s not just a recipe; it’s a high-security clearance operation.
Monitoring and Audit Trails: The Paranoid Overlord’s Toolkit
Ah, monitoring and audit trails — the final frontier in our quest for over-engineering. Why simply trust that your website is running smoothly when you can obsess over every metric, log, and user action? Let’s dive in.
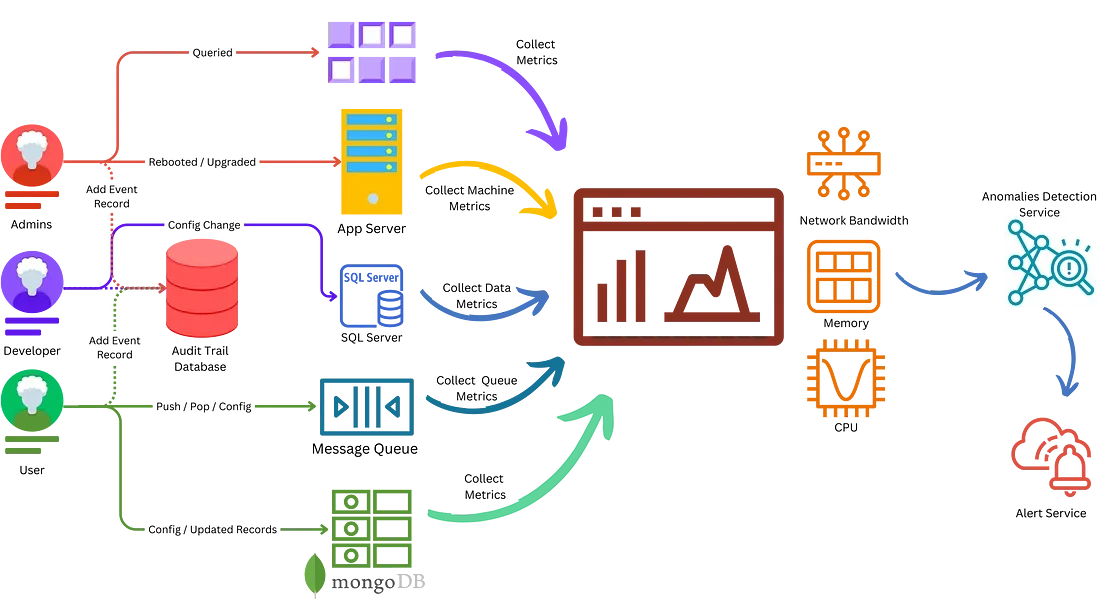
Monitoring Service: The Overzealous Watchtower
First up, monitoring services. Implement a comprehensive monitoring solution that tracks every conceivable metric. CPU usage, memory consumption, network latency — you name it. Set up alerts for thresholds that will never be reached, like triggering a warning if CPU usage goes above 1%. Because clearly, your grandma’s cookie recipe website is as resource-intensive as a cryptocurrency mining operation.
Audit Trails: The Digital Footprints to Nowhere
Next, let’s talk about audit trails. Integrate an audit trail system to log every action taken on your website. Who viewed a recipe? Who added a new comment? Who failed the MFA for the chocolate chip cookie recipe? Log it all. Store these logs in a separate, highly secure database that requires biometric authentication to access. Because you never know when you’ll need to trace back the exact sequence of events that led to someone spending 3.2 seconds hovering over a recipe.
Caching Strategies: The Illusion of Efficiency in a World of Excess
Ah, caching — the art of storing copies of files in a temporary storage location so they can be more quickly retrieved. But in our over-engineered world, why stop at mere efficiency? Let’s explore the myriad ways to make caching as complex as possible.
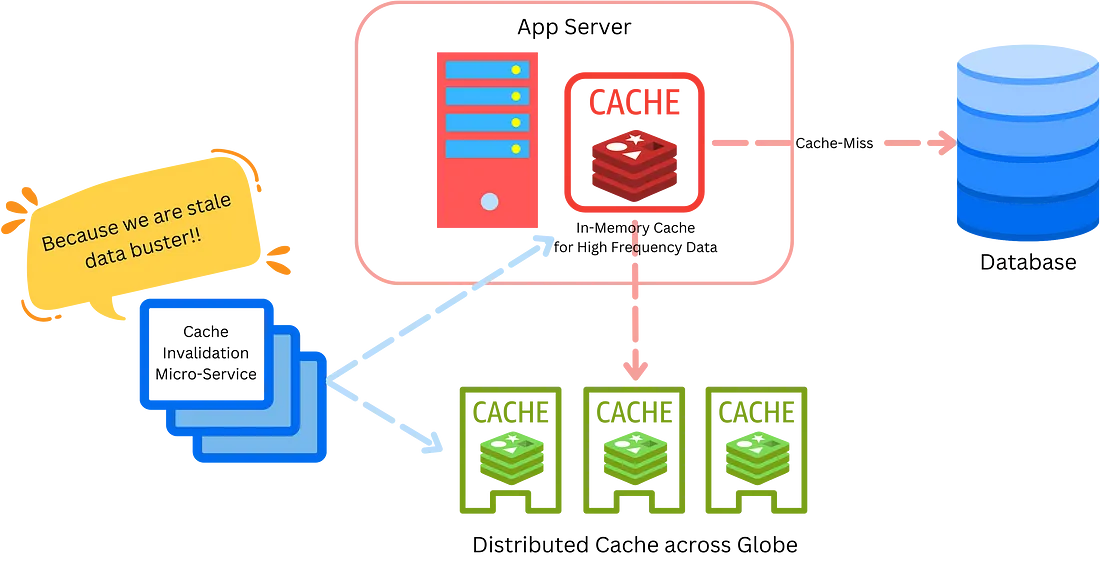
Multi-Level Caching: The Russian Nesting Dolls of Data
First up, multi-level caching. Implement not just one but multiple layers of caching. Use an in-memory cache like Redis for the most frequently accessed data and a distributed cache for less critical data. Because why have one cache when you can have a cache for your cache?
Cache Invalidation: The Sisyphean Task
Next, let’s talk about cache invalidation. Implement a complex strategy that involves time-based, usage-based, and event-based invalidation. Create a separate microservice to manage your cache invalidation logic. Nothing says “I’m an expert in caching,” like making removing data from the cache as complicated as possible.
Conclusion: The Symphony of Over-Engineering
And there you have it — a guide to building a simple website for your grandma’s cookie recipes that’s so over-engineered it could run a small country. We’ve journeyed through hosting, APIs, data streams, databases, full-text search engines, security measures, monitoring, audit trails, and caching strategies. It’s been a wild ride, and I couldn’t be happier to share this adventure with the developer community.
Remember, the sky’s the limit when it comes to over-engineering. So unleash your inner architect and build something unnecessarily complex today!
Articulo tomado en su totalidad de https://blog.devgenius.io/the-art-of-overkill-web-dev-edition-6f224d81d9e9